Dive Brief:
- United States officials are investigating multiple cyberattacks that unsuccessfully targeted nuclear generation sites sometime this year, E&E News reports. The event has been code named "Nuclear 17."
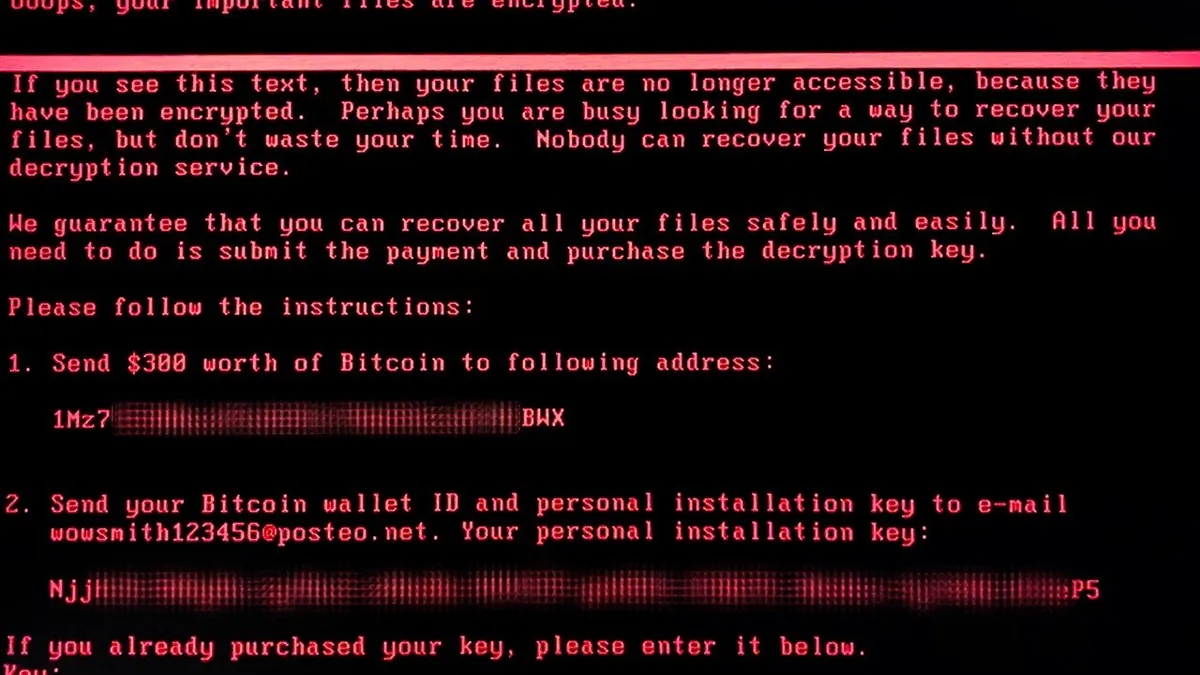
- News of nuclear cyberattack attempts in the U.S. broke as a wave of ransomware attacks was spreading across parts of Europe, similar to the WannaCry virus that surfaced in May. The new attacks shut down decommissioning operations at the Chernobyl nuclear site, though U.S. officials said there were 'no indications' the malware targeted North American power operations.
- Cybersecurity has become a major priority of the electric utility industry. Last month, cybersecurity firm Dragos issued a report concluding malware that was used in a 2015 cyberattack resulting in power outages in Ukraine could be modified by developers to target the United States.
Dive Insight:
After a day of malware spreading throughout Europe, the North American Electric Reliability Corporation said it appeared the attacks did not target U.S. firms.
"There are no indications of any similar attacks in North America," a NERC spokesperson told the Washington Examiner.
Tuesday afternoon, malware was infecting computers around Europe. The virus forced decommissioning activities to be halted at the Chernobyl site, and has impacted banks, airlines and a wide range of corporations.
Ukraine appeared among those hardest hit, with The New York Times reporting the national power grid company Kievenergo "had to switch off all of its computers because of the attack," though the company now has the situation under control.
Russian hackers were behind a cyberattack on the Ukrainian grid in 2015, but the Times reports that its firms were targets of this recent round of malware as well, with energy giant Rosnoft also affected.
NERC's comments mean that the Tuesday malware attacks are separate from multiple cyberattacks targeting U.S. nuclear operations that E&E News reported on the same day. The news outlet has not yet identified any generator that has been impacted and reports much of the information may be classified.
A NERC spokesperson told the outlet that the group "is working closely with the government to better understand any implications this incident might have for the electricity industry."
The news organization said it reached out to almost two dozen nuclear plant owners, but said most offered little comment.
The Ukraine attack in 2015 resulted in a widespread power outage, but so far the United States has been able to keep its system protected. However, the report from Dragos indicated that same software could be modified to attack domestic power systems.
Dubbed "CrashOverride," the malware is just the second industrial control system-tailored malware to target physical industrial processes, according to Dragos.
Lloyd's of London in 2015 issued a report aimed at informing the insurance industry as to the potential impacts of a widespread attack on the U.S. power grid, and concluded the total economic loss could range from $243 billion up to $1 trillion in the most damaging scenarios.
The North American Electric Reliability Corporation held a simulated attack on the United States grid infrastructure in 2015, finding that communication between the utility industry and federal government needed to be improved, among other recommendations.
Utilities are taking notice of the warnings. A Utility Dive survey of more than 600 sector executives at the beginning of 2017 revealed that security issues are the most pressing concern for the sector this year. In both 2015 and 2016, security issues ranked outside of the top five concerns.
This post has been updated to include comments from a NERC spokesperson given to the Washington Examiner.