The ongoing expansion of the U.S. electric vehicle ecosystem is creating new cybersecurity risks for the nation's power system by offering hackers access through widely distributed and less well-protected charging stations, but solutions are emerging, charger software providers and researchers said.
Recent hacks using Russian charging stations to ridicule Vladimir Putin and British chargers to play adults-only content show cyber threats are real, public and private sector analysts said. Accessing customer personal or financial data has been demonstrated, and an EV boom driven by proliferating transportation electrification policy goals could spread threats across the power system, they added.
With a Biden Administration goal of 50% of new car sales to be zero emissions by 2035 and funding for a national EV charging network, U.S. transportation electrification“is accelerating at a breakneck speed,” said Joseph Vellone, North America head for international charger software provider ev.energy. Innovative utility-managed charging programs could allow “an attacker with malicious intent to destabilize the power system,” he said.
“Permissive access to chargers was adequate for traditional power systems,” but “vehicle-grid integration” to manage charging “adds orders of magnitude of operational complexity,” added Duncan Greatwood, CEO of cybersecurity specialist Xage. Vulnerability is significant because “cybersecurity strategies were only introduced into the energy sector in the last 18 months,” he said.
EVs, now about 1% of the 250 million U.S. light-duty vehicles, rose to 6.1% of new U.S. vehicle sales in Q3 2022 from 3.7% in Q3 2021, Clean Technica reported September 13. By 2030, they could be 52% of new car sales, according to a BloombergNEF estimate reported September 20. And vulnerabilities will increase with that rapid EV ecosystem expansion across the power system’s attack surface, cybersecurity specialists agreed.
Those vulnerabilities threaten more serious impacts than ridiculing Putin or randomly showing adult content, power industry, private cybersecurity providers, and cybersecurity research leaders said. An October 25 Office of the National Cyber Director-led forum recognized that new answers for EV ecosystem cybersecurity are needed. But stopping Black Hat attackers with financial or worse motives who seem always a step ahead will be challenging, those leaders acknowledged.
Detailing the threats
The U.S.’s over 122,000 total public charging ports and its 455,000 new EV sales in 2022 led the individual country rankings in the BloombergNEF EV Dashboard released September 21. And “people are plugging in and charging without attacks,” said Sunil Chhaya, a senior technical executive for transportation at the Electric Power Research Institute.
But “hackers are everywhere,” and the growth and visibility of the EV ecosystem will magnify the temptation to either make money or a political point,” Chhaya said. “The consequences of threats not addressed are real” because “charging infrastructure is a good entry point” for financial, EV ecosystem, or power system attacks, he added.
The EV ecosystem is part of a growing “internet of energy” market that will support the energy transition but comes with the “side effect” of an increased attack surface, agreed Schneider Electric VP for Product Cybersecurity and Chief Product Security Officer Megan Samford.
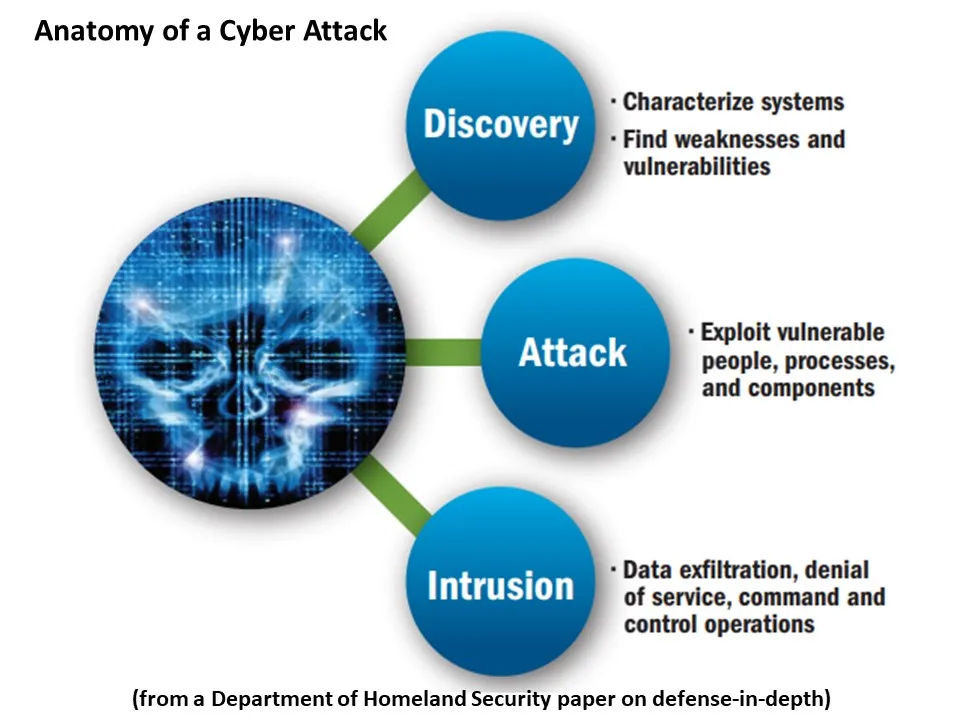
Most recent attacks focused on vulnerabilities between utility-owned power system assets and chargers to obtain customer personal and financial data or disrupt charging, Samford said.
Few specifics on attacks are made public, but in addition to the Russia and U.K. events, a white hat attack on German Tesla charging stations was reported by Bloomberg News January 11. In addition, international researchers identified 13 vulnerabilities in 16 charging systems, TechRepublic reported March 23. Finally, out of more than 240 attacks on charger stations globally in 2021, 40.1% used charger access to get at charger company servers, according to Israeli EV cybersecurity specialists Upstream’s 2022 report.
Without early detection, attacks such as these could lead to “cascading” power system outages, Samford said.
Too often, cybersecurity is “an afterthought” in connecting public charging to the power system, according to a 2019 EPRI comprehensive cybersecurity plan. But planning should include principles of data confidentiality, including protections to access and acknowledgment of risks to safety, privacy, reliability, and finance.
Charging stations provide increasingly complex interactions about when and how quickly vehicles are charged and discharged, said Xage’s Greatwood. “The easiest hack is not vertically into the well-protected power system core but horizontally to spread malware across less well-protected EV charging stations and station management systems,” he added.
“The energy transition is making grid edge assets more important,” he said. “A successfully widespread attack could stop traffic” or “create a local outage that leads to a cascading power system disruption,” he agreed.
Distribution system infrastructure like substations are difficult to attack and system voltage and frequency are carefully monitored, said Rolf Bienert, managing and technical director of leading power system standards advocate OpenADR Alliance. But as smart chargers and real-time pricing are used to address demand spikes, attackers might disrupt communications to create reliability failures, he said.
The charging system’s ready public access through remote physical connections, its limited designed-in security, and its expansive attack surface makes it “by far the most vulnerable element” in the EV ecosystem, Roy Fridman, CEO of Israeli cybersecurity specialist C2A Security, summarized in a July 4 blog.
Software “is the connective tissue between utilities and system operators” allowing management of EV charging “to balance loads,” said ev.energy’s Vellone. But EV charger software “could carry a Trojan horse planted by a rogue agent or nation like Russia or China,” he agreed.
In a state with a heavy charging load like California, the attacker “could orchestrate a sudden huge power surge during a peak demand period that could easily be catastrophic,” Vellone said. Cascading circuit outages “could result in something like the August 2003 two-day blackout across the Northeast caused by a fallen tree branch,” he suggested.
U.S. cybersecurity standards like federally-ordered Zero Trust and Defense in Depth strategies are inadequate for fully protecting financial and personal data or regulating charger firmware and software, Vellone and others said.
“The gold standard is the 2018 European Union General Data Protection Regulation’s strict, comprehensive, and forward-looking guidelines,“ and U.S. federal legislation could use the 2018 California Consumer Privacy Act as a template, Vellone said.
Cybersecurity efforts like the General Services Administration’s May 2021 Executive Order 14208 and President Biden’s October 11 Executive Order offer no guidance for the EV ecosystem, stakeholders agreed. And payment card industry security standards for gasoline pumps omit critical EV charger vulnerabilities that should be addressed by the North American Electric Reliability Corporation, they added.
Utilities were quick to answer Utility Dive queries about their cybersecurity efforts but, for good reason, reluctant to detail incidents or the growing threat potential.
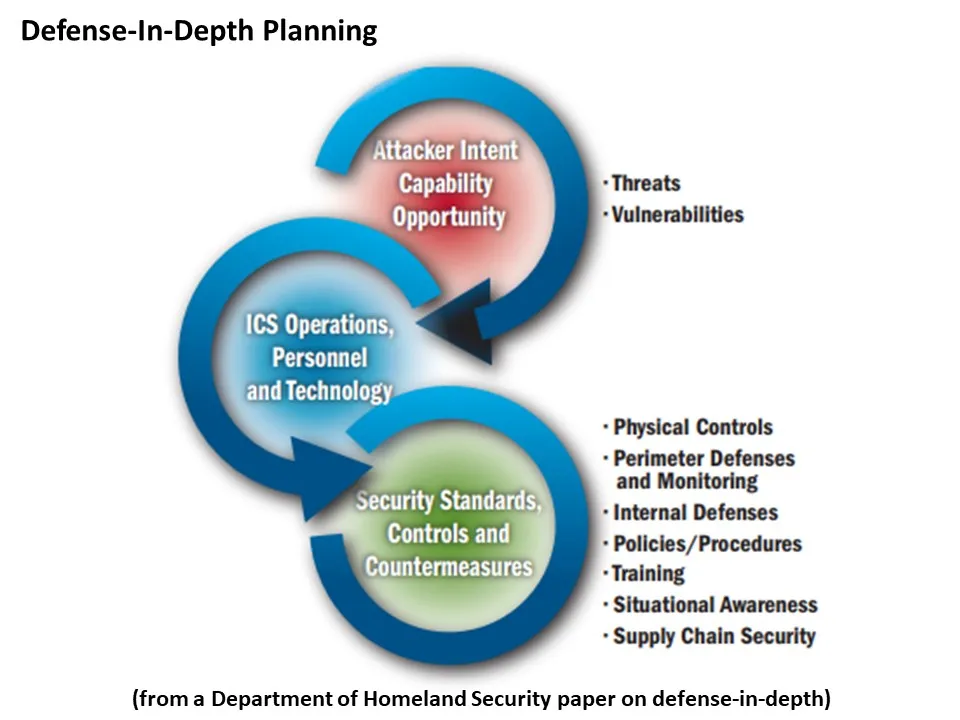
The utility dilemma
A conundrum limits utility and system operator public comments on cybersecurity. They want customers and shareholders to know they are aware of and working on solutions to threats, but they cannot detail experiences and preparations because it could reveal their enormous attack surfaces’ vulnerabilities, they unanimously agreed.
“We would rather not provide details on particular threats,” said Consolidated Edison spokesperson Allan Drury. But ConEd’s experts and government and industry partners are helping develop “a robust defense-in-depth program to mitigate the threats,” he added.
Federal cybersecurity guidance describes a defense-in-depth strategy for charging stations as multiple layers of automated authentication and operations monitoring from the utility to the charger, C2A’s Fridman and other security providers said.
DTE Energy vehicle-grid integration programs include open access software platforms, but “we coordinate extensively with our industry partners on cybersecurity,” was all DTE Energy Spokesperson Angela Meriedeth could disclose.
“For obvious reasons, San Diego Gas and Electric does not discuss specifics of our security efforts,” Krista Van Tassel, the utility’s spokesperson, echoed. But “critical systems” are “rigorously” tested for vulnerabilities, security practices and tools are “continually” reviewed, and the utility is working with industry partners on “risk mitigation strategies,” she added.
Southern California Edison is similarly working with industry stakeholders to develop cybersecurity “standards and protocols” to “reduce cybersecurity risk to the grid as EVs continue to grow,” the utility’s spokesperson Brian Leventhal said.
Washington state’s Avista Utilities does not now face a significant cyber threat because chargers and utility control systems are not interconnected, Rendall Farley, its manager of electric transportation, said. But future programs and a “next generation of high-powered chargers” may interconnect utility systems through managed charging to address demand peaks, which would require “mitigating any cyber threats,” he said.
Strategies to mitigate such vertical attacks on utility control systems from public chargers and to securely update cybersecurity software and firmware are being developed, researchers and private sector experts agreed.
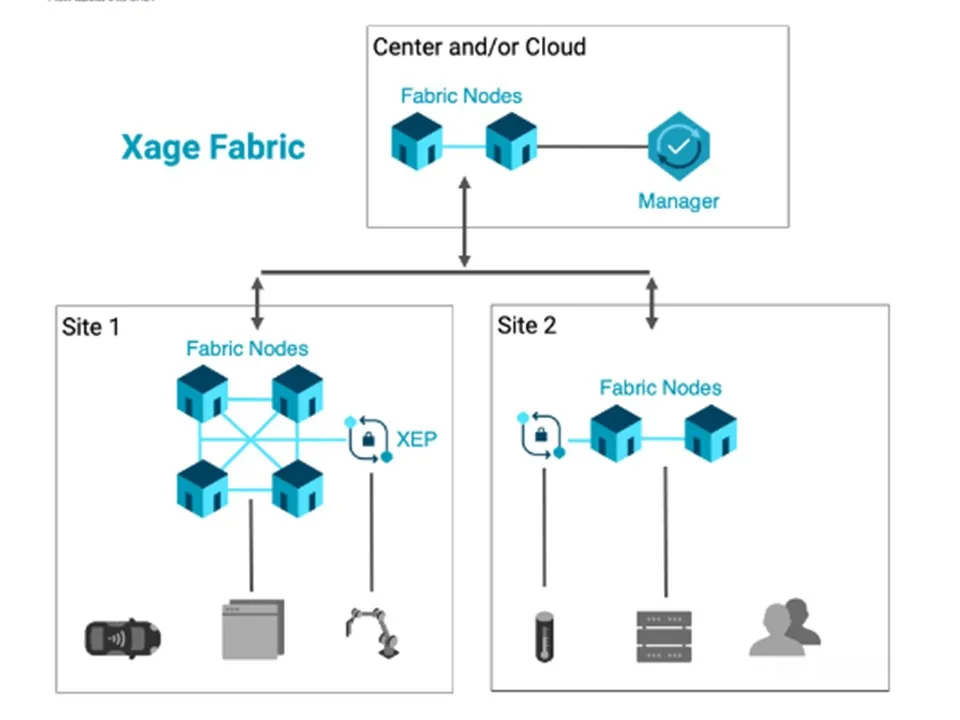
Emerging strategies and tools
Many utilities are planning to manage EV charging loads, which will increase vulnerabilities to cyberattacks, most stakeholders agreed. But funding and research are already addressing the challenge, many said.
“The five-year $5 billion funding of a national interstate charging corridor in the Infrastructure Law “is a once in a generation opportunity,” said Idaho National Laboratory Senior Research Engineer Tim Pennington. It can lead to “important new cybersecurity standards” from federal agencies, he added.
Charger hardware can have “independent certifications” for meeting cybersecurity standards, be programmed with “self-aware, built-in, security capabilities,” and be given routine “system checks,” Schneider Electric’s Samford said. But capabilities are still needed to “detect anomalous behavior across the network and system,” to identify “potentially malicious behavior,” and to “take action,” she added.
INL is developing those capabilities within the Department of Energy’s Cybersecurity, Energy Security, and Emergency Response, or CESER, programs, Pennington said. And its laboratory demonstrations have shown the new strategies and technologies can work, he added.
There is “no official specific intelligence about an adversary or a threat,” INL Energy Threats Program Manager Jamie Richards, working under the CESER programs, specified. But laboratory demonstrations with high-powered chargers showed a new tool can detect and mitigate attacks, she added.
One INL demonstration showed charger vulnerabilities like a piece of readable code, a default password, or an accessible public charger port make serious impacts possible, Richards said. In a second demonstration, INL’s safety instrumented system, or SIS, cybersecurity tool, “recognized adversary behaviors targeting those charger vulnerabilities with a 75% success rate,” she added.
INL is now testing automated SIS interventions like interrupting charging to prevent escalating impacts, Richards said. The SIS tool’s cost-effectiveness “is hard to know at this stage” because “the return on investment for any security solution is not typically justified until the cost of what it can prevent becomes clear,” she added.
A coming but not yet announced EPRI online tool will allow EV ecosystem participants “to assess their cybersecurity strengths and weaknesses and obtain mitigations based on related industries’ best practices,” EPRI’s Chhaya said.
But best practices from other industries may not provide the cybersecurity needed for the EV ecosystem, Xage’s Greatwood said. “Banks can use manufacturer-installed security certificates in laptops and cellphones, but that level of authentication is not built into today’s EV charging systems,” he said.
A Mesh Architecture defense strategy could provide a higher level of cybersecurity by storing user identity authentication information in multiple, programmed internet “nodes,” he said. “If two nodes of a 20-node Mesh are hacked, the other nodes will recognize the intrusion and deny further access to the hacker to maintain a distributed system’s integrity,” Greatwood added.
“In traditional operational security, the system is as weak as its weakest link and one hack creates access to the entire system, he said. With a Mesh architecture, hacked nodes are “quickly identified and reset,” which means “more nodes in the Mesh makes the system’s security better,” he added. “No protection can be guaranteed, but the Mesh approach makes attacks more difficult and impacts more limited,” he said.
“It is always a cat and mouse game,” EPRI’s Chhaya agreed. “The objective is to combine practices that generally perform securely except for isolated incidents and use them to minimize malicious intrusions and their impacts” because none of the participants in the EV ecosystem “want to end up causing an issue and being in a headline,” he said.
Vellone, whose priority is achieving the 2030 clean transportation mandates, agreed. “Cybersecurity for hardware and software needs to come together at the same time to make this happen and perfect cannot be the enemy of good,” he said. “The commitment must be to continuous proactive improvement and securely updating everything over and over,” he added.
Correction: A previous version of this story mischaracterized the type of power disruption cyberattackers could potentially orchestrate. The concern is over attackers orchestrating a power surge during a peak demand period.





















